- Status
- Online
- Joined
- Oct 22, 2024
- Messages
- 548
- Reaction score
- 151
Hello everyone! Remember that base for Warzone from SbaGGy that I posted? Now there’s a fresh source for Warzone Black Ops 6 from February 22, 2025. It only works in Warzone. The regular version of the game won’t work. And here, you also need your own kernel driver. You can’t really do without it in any game or any source (thanks to isnq for the base!). But let’s take things one step at a time.
What are Chams?
Chams is a cheat feature for Call of Duty that highlights enemies through walls. Simply put, the game renders enemies on top of walls, and you can see them. It looks something like this:
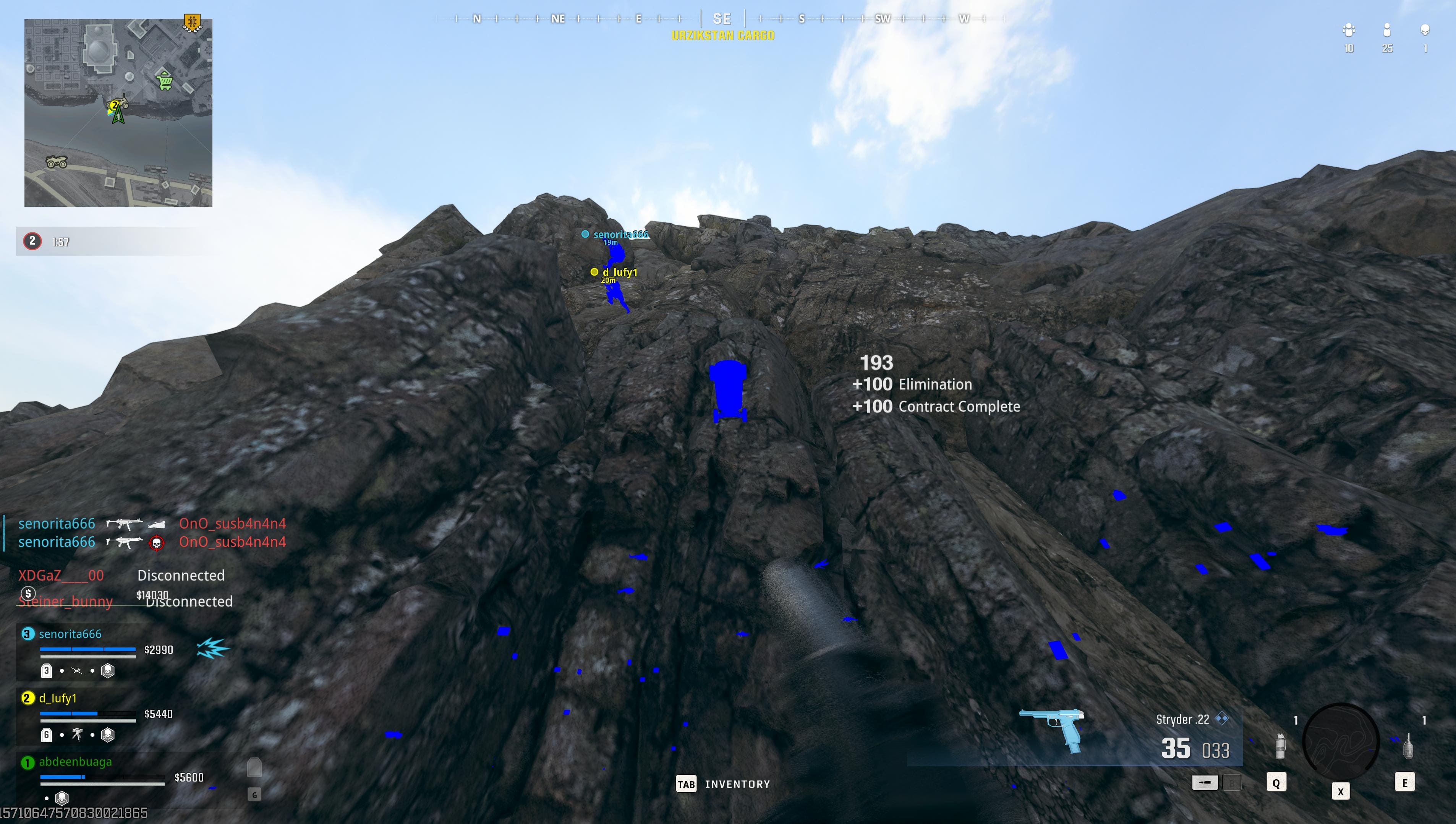
Besides having a wallhack, this base is also suitable for writing your own hack. It has pretty clean and understandable code, updated for the latest Warzone patches, FPS doesn’t drop, and it works without crashes. So you can use it as a foundation for your own project.
How does it work?
It’s all based around the
R_AddDObjToScene hook. This is a function in the game that handles rendering objects. The hack modifies it, adding highlights to enemy models. But there’s a catch:- A kernel driver is mandatory. Without it, the anti-cheat will ban you in a second.
- Only Warzone. In regular Black Ops 6, the engine logic is different, and the cheat will break the game.
- A little tip: even though the hack was just recently posted, don’t forget to use a spoofer for your account.
Download Chams cheat for Black Ops 6
View hidden content is available for registered users!
What type of cheat is this: External or Internal?
The original source (available via the link above) is internal, but some skilled folks (thanks to beck123x) tweaked it and turned it into an external one. Sharing it with you:
C++:
void InjectShellcode() {
BYTE shellcode[] =
{
0x48, 0x8B, 0x44, 0x24, 0x30, //mov rax, [rsp+30]
0xC7, 0x80, 0x50, 0x00, 0x00, 0x00, 0x00, 0x00, 0xFF, 0xFF, //mov dword ptr [rax+50], 0FFFF0000
0xC6, 0x80, 0x5C, 0x00, 0x00, 0x00, 0x01, //mov byte ptr[rax+5C],1
0xC6, 0x80, 0x5D, 0x00, 0x00, 0x00, 0x01, // mov byteptr[rax+5D],1
0xC6, 0x80, 0x5F, 0x00, 0x00, 0x00, 0x01, // mov byte ptr[rax+5F],1
0xC6, 0x80, 0x60, 0x00, 0x00, 0x00, 0x00, // mov byte ptr[rax+60],0
0xC6, 0x80, 0x68, 0x00, 0x00, 0x00, 0xB2, // mov byte ptr[rax+68],-78 (5000)
0x55, // push rbp
0x41, 0x54, // push r12
0x41, 0x55, // push r13
0xE9, 0xC7, 0xC2, 0xBD, 0xFE // jump back to original function + 0X05
};
BYTE JumpToShell[] =
{
0xE9, 0xFD, 0x3C, 0x42, 0x01, 0x90
};
uintptr_t codecave = base_address + 0x79339A2;
uintptr_t originalFunction = base_address + 0x650FCA0;
mem::write_physical((PVOID)codecave, shellcode, sizeof(shellcode));
mem::write_physical((PVOID)originalFunction, JumpToShell, sizeof(JumpToShell));
}
Last edited: